Evolphin Zoom supports OIDC natively. However many Identity Providers (IdP) only support older SAML2 standard for federating with other IdPs. For example if you were using Azure AD as your OIDC provider for Zoom, but needed to provide Zoom Web app access to partners/freelancers that were using Google’s G Suite, you will need to federate Azure AD using SAML2 with G Suite, as that’s the only way Microsoft and Google currently support it. In this article we will look at how to setup custom SAML2 direct federation between Microsoft Azure AD (Zoom OIDC Provider) and Google G Suite IdP. The concepts here can be generalized to any ODIC provider integrated with Evolphin Zoom.
If you wish to setup authentication directly with Google G Suite using OpenID Connect flow, head over to this page.
Prerequisites
- OpenID Connect with Azure AD is already setup as per the help article.
- You have administrative access to Google G Suite account
- You have administrative access to Azure AD tenant
- You have reviewed and understood this Azure AD help article completely
End-user Single Sign On experience
With direct SAML2 federation, guest users will attempt to sign into the Zoom connected Azure AD OIDC tenant using their own G Suite organizational account. When they are accessing a Zoom Web or Desktop app and are prompted for sign-in, direct federation users are redirected to Google G Suite IdP. After successful sign-in, they are returned to Azure AD to access Zoom apps. Direct federation users’ refresh tokens are valid for 12 hours, the default length for pass through refresh token in Azure AD.
First configure the G Suite SAML App
Step 1: Head over to https://admin.google.com/ac/apps and login using your G Suite admin credentials and click on SAM Apps

Step 2: Create a new custom SAML App, by clicking the + icon an the bottom of the page

Step 3: And then select the “Setup my own custom app” option

Step 4: Download the IdP metadata using Option 2:

Step 5: Enter the basic information such as a name for the SAML Federation:

Step 6: Provide Azure AD details as a SAML2 Service Provider (SP). In this flow Azure AD is acting as the SP to G Suite as the IdP for purposes of federation. Ensure the ACS URL is: https://login.microsoftonline.com/login.srf and Entity ID is: urn:federation:MicrosoftOnline. Rest of the fields need to be as below:

Step 7: Click of next and add a new Attribute mapping, with Google IdP “Primary Email” attribute mapped to Azure AD Federation attribute name: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress. Click Finish to save the SAML app setup in G Suite:

Optionally turn it on for everyone in G Suite organization:

Configure direct federation in Azure AD
You will need the G Suite IdP metadata file you downloaded (see above) before you start.
Step 1: Click on New SAML/WS-Fed IdP option:

Step 2: Form entries: Select SAML, enter the domain name for G Suite and select the G Suite IdP metadata file:

Step 3: Click Parse to automatically fill-in rest of the form fields:

Step 4: Save the form entries
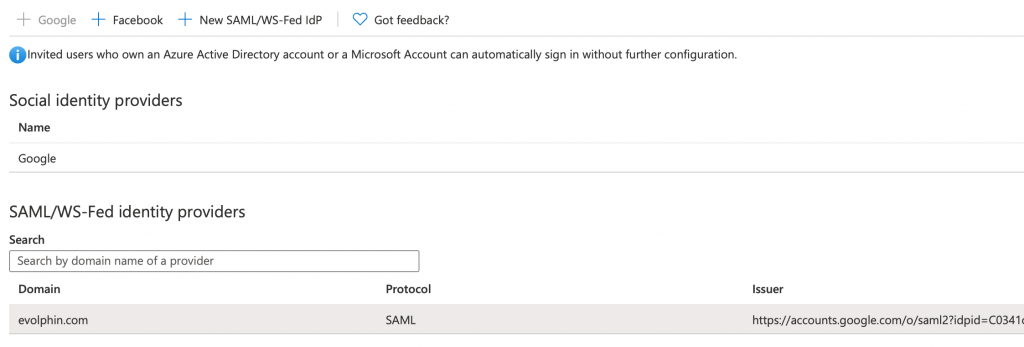
The above steps can be repeated for each new direct federation that needs to be setup between Azure AD OIDC provider acting as an SP to a SAML 2 IdP.
That’s it, now go ahead and invite a G Suite user as a New Guest user in your Azure AD and follow the steps to pull the invited guest users into Zoom Managed Accounts via the Zoom Web Admin. From there follow the usual steps to configure the guest users as a web only concurrent user, assign them roles or add them as a member of project vaults.